Cyberintruder
Summary
Cyberintruder is my graduation project, created in partnership with my client, Gert Douma, an ICT security officer at Hanze. This innovative product highlights the various cyberthreats present in the digital environment and their potential impacts. Through immersive gameplay, users encounter a series of cybersecurity challenges, offering a hands-on, learn-by-doing experience that deepens their understanding of online security.
Target audience
- 1st-year CMD students at Hanze University of Applied Sciences
- ~20 years old
- High-experienced with gaming
- Low-experienced with cybersecurity
Development process
The product has been developed across ~6 months, following the general design cycle:
1. Orientation & Understanding
In the Orientation and Understanding phase the main objective was to gather enough information that could grant me the necessary knowledge to translate the research into game design field. The methods used in this phase:
- 1.1. Client interview
The client interview was conducted in the first week of September, being the first method used to understand the problem context and my client’s needs and requirements.
- 1.2. Cybersecurity desk research
A detailed study was conducted on cybersecurity, covering its core concepts, threats, prevention methods, types of cyber-attacks, hackers, hacking techniques, history of cyber-attacks, and tools used. The goal was to provide clear and useful information to better understand the field and make it easier to address related challenges in the future.
- 1.3. Serious games desk research
The desk research method on serious games was conducted to help me understand games designed for teaching and educating. Key findings from this method include Baaden et al.’s (2018) study, which identified rules for creating and improving serious games.
- 1.4. Competitive Analysis – Serious Games
To better understand how products in my area of interest function, a competitive analysis was conducted, focusing on serious games. Several serious games were reviewed, and key insights were organized into bullet points.
- 1.5. Behavioral change desk research
One key point raised by my client during our first interview was that students show little interest in the information they get from the survey, leading to no changes in their behavior. To better understand how to encourage behavior change, a literature review on behavioral change was carried out. The main findings come from a research done at Liverpool John Moores University (2011).
- 1.6. Target audience questionnaire
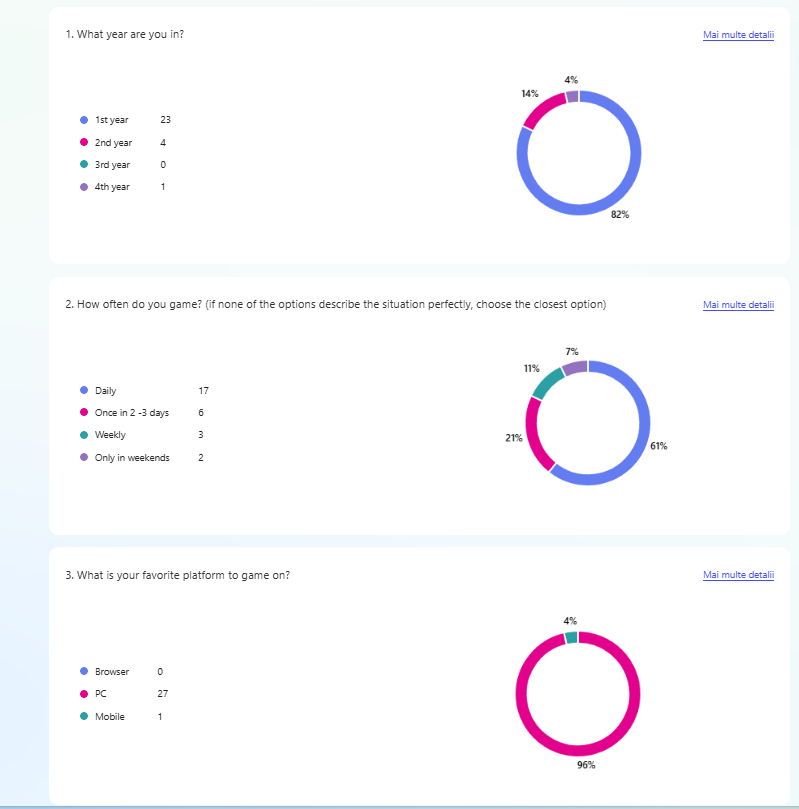
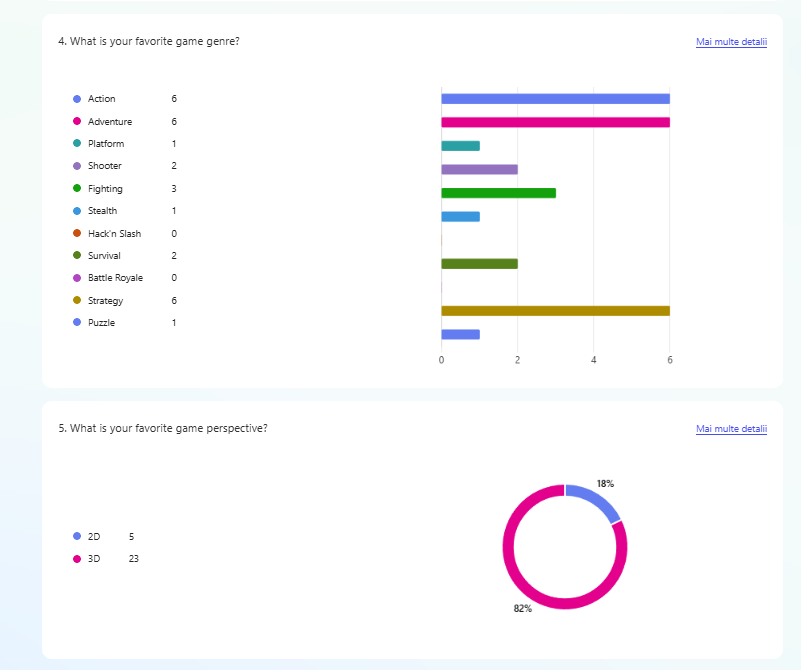
After gaining a clear understanding of the problem and the product’s context, I created a questionnaire. Its goal was to identify what the target audience needs and enjoys about games, helping shape the design direction for the next steps. The questionnaire was shared with the target audience during the Test’n Chill session at Hanze University of Applied Sciences, where 28 students participated.
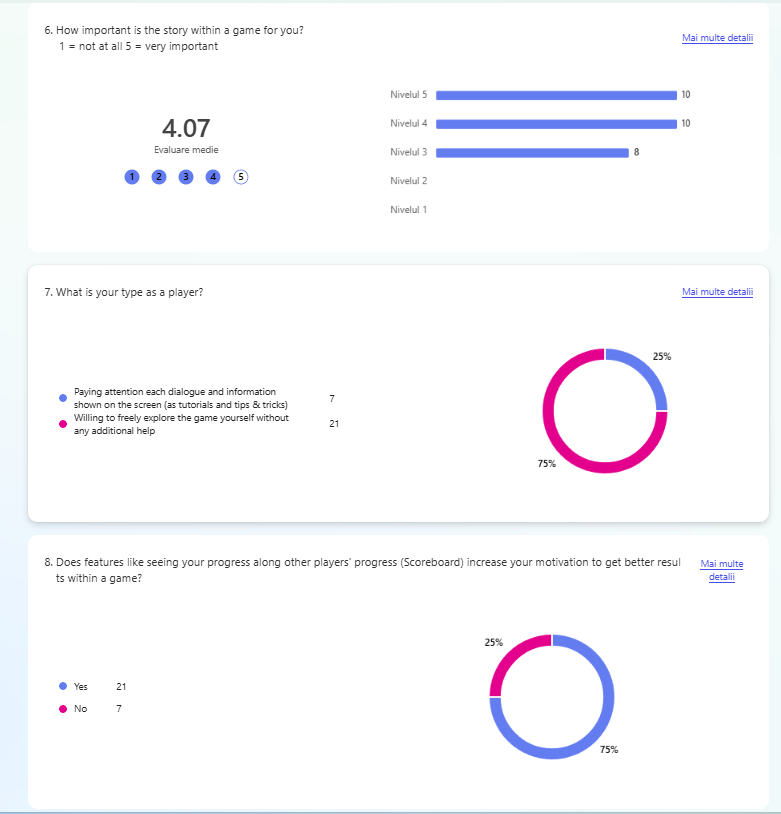
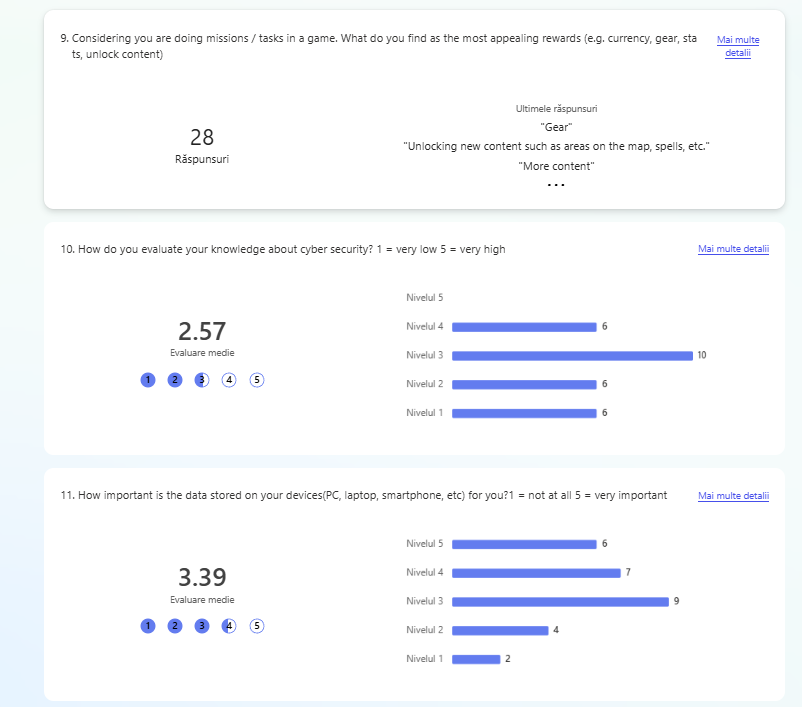
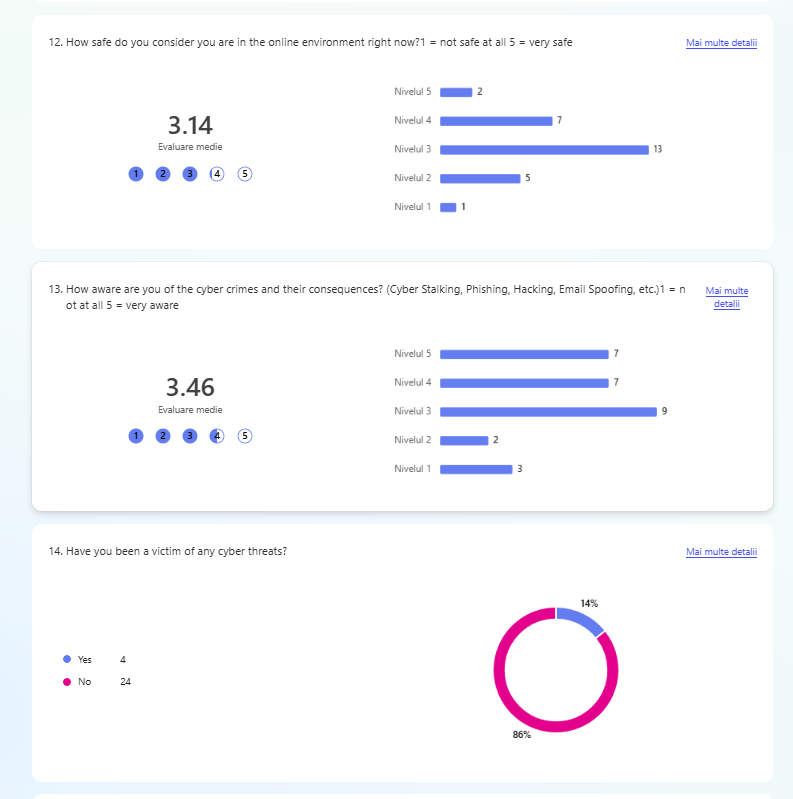
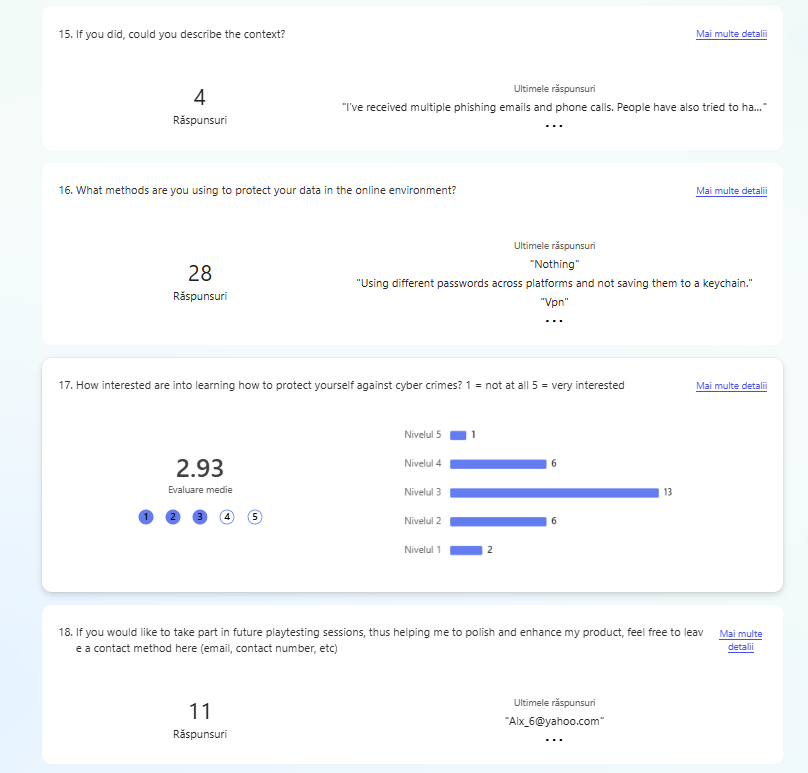
- 1.7. Adventure games desk research
After reviewing the questionnaire results, I chose to place my product in the adventure genre. As a result, I conducted a literature study on adventure games based on Rober (2014).
- 1.8. Competitive analysis adventure games
Once the main elements of creating adventure games were identified, a second analysis was done.
This analysis focused on how adventure games handle their introductions, the number of characters in the story, how missions or challenges are tracked, and the average time needed to complete the game.
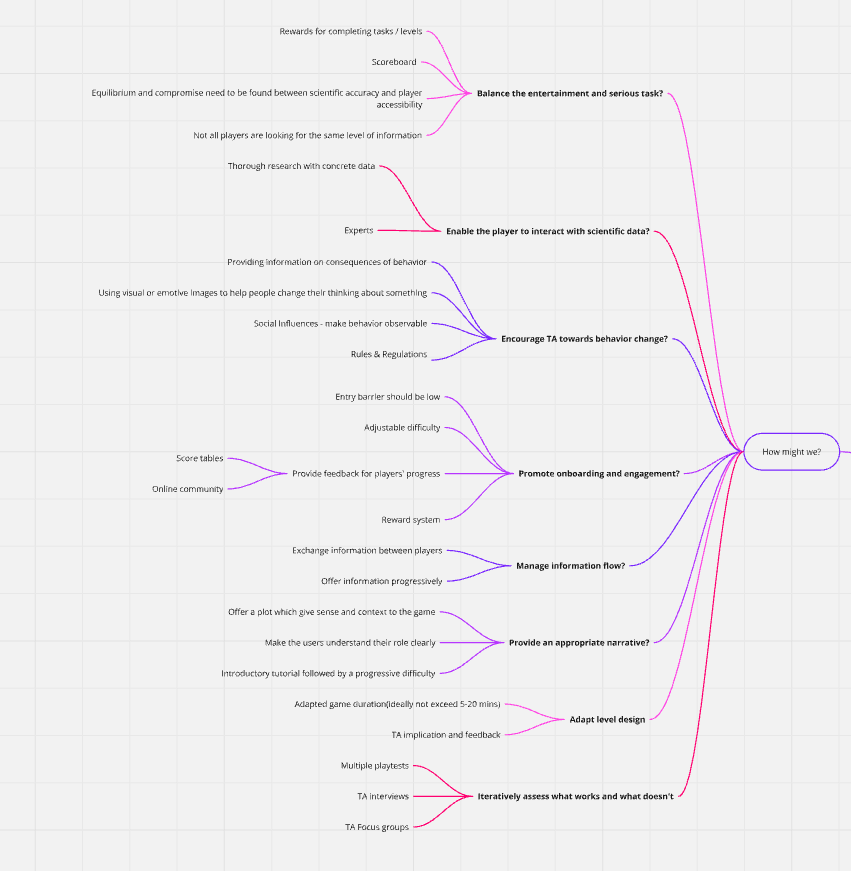
- 1.9. How Might We
After gathering the needed information, the “How might we” method was used. This approach helps define solvable problems starting with the “How might we” statement. It allowed me to identify solutions and address gaps in my work.
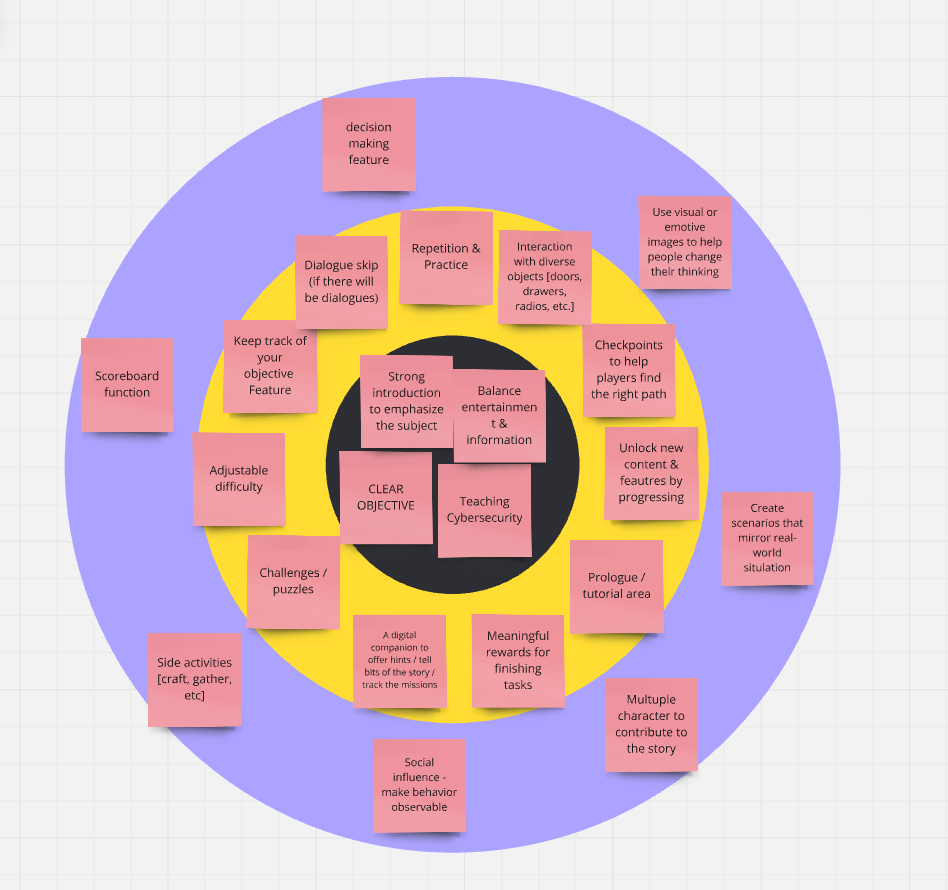
- 1.10. Bull’s Eye Diagram
To compare the number of meaningful ideas from the methods discussed earlier, the Bull’s Eye Diagram method was used. This method organizes ideas based on their importance to the project. The ideas are placed within three circle layers: critical (center), important (middle circle), and peripheral (outer circle).
2. Concepting
For the concepting phase, two methods have been used.
- 2.1. Brainwriting method
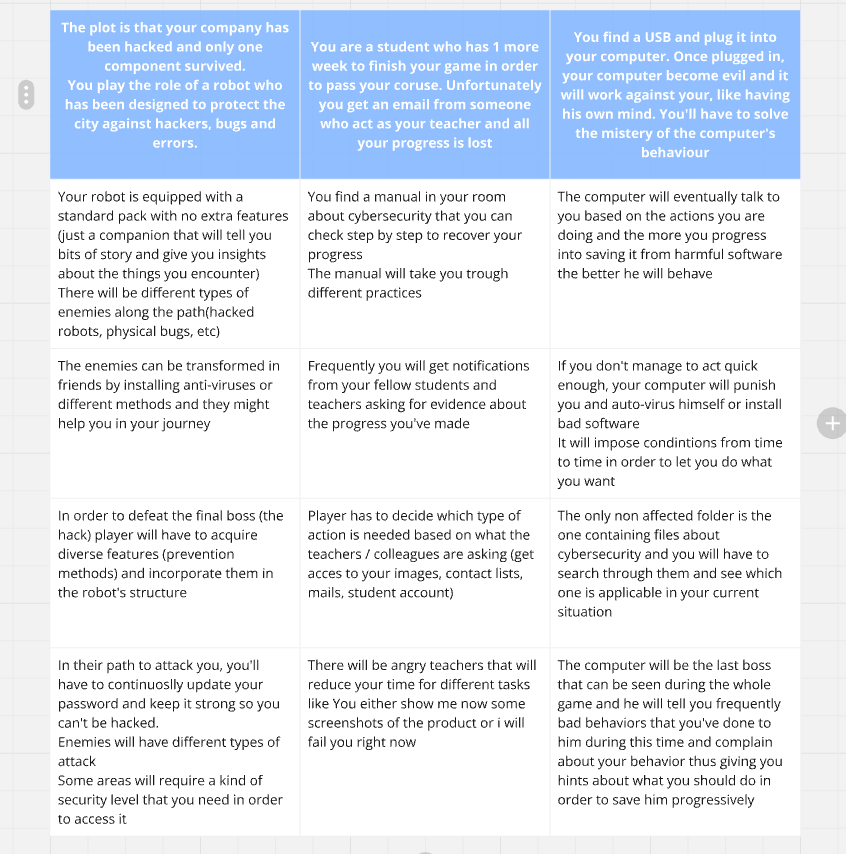
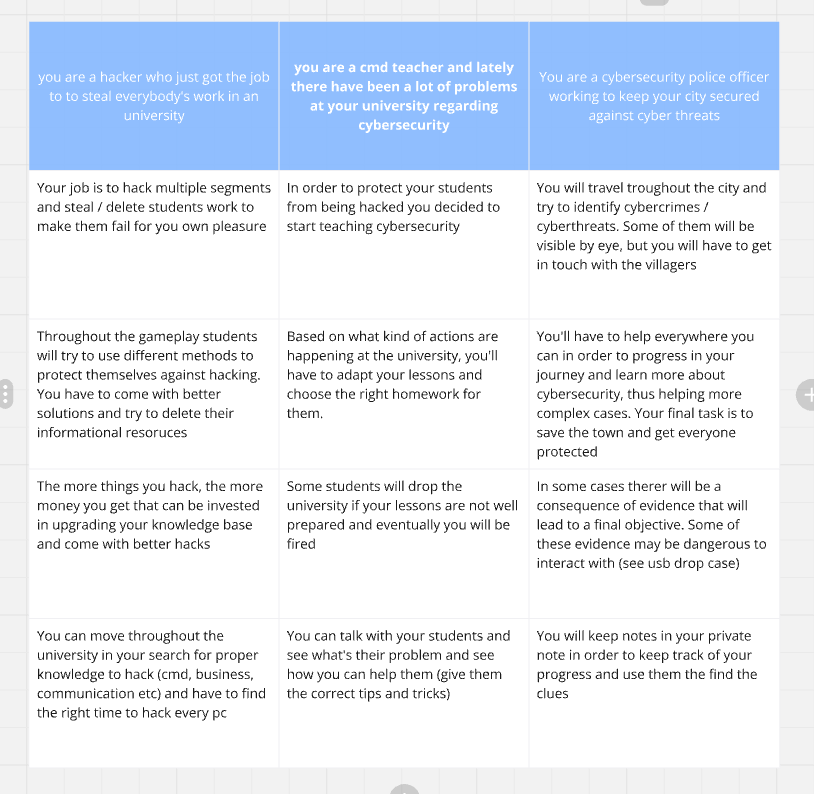
The brainwriting method was used to generate a variety of concepts. In this team-based approach, each person starts by writing down 3 ideas within 2 minutes. Then, every 2 minutes, participants add one idea to each of the original concepts until everyone has contributed to all ideas.
This process was repeated 5 times, reflecting the typical team size based on my experience as a student. In the end, a total of 15 concepts were produced.
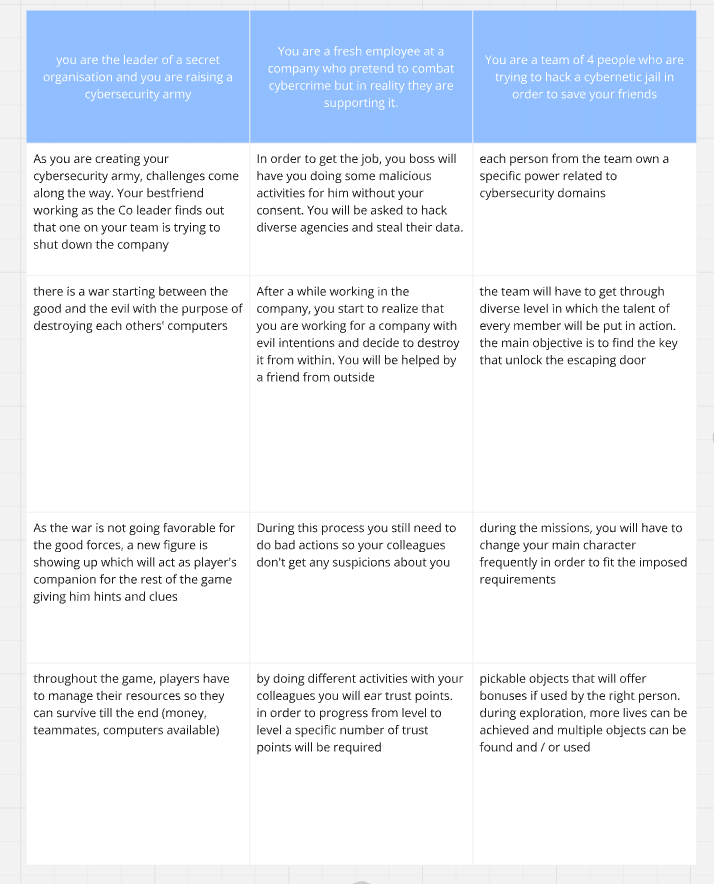
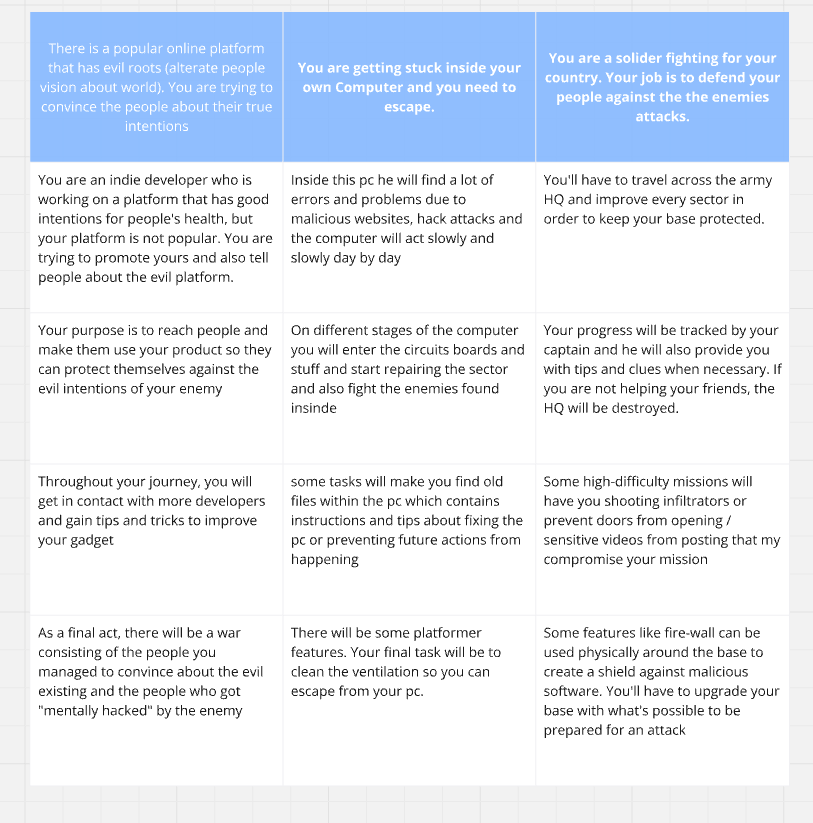
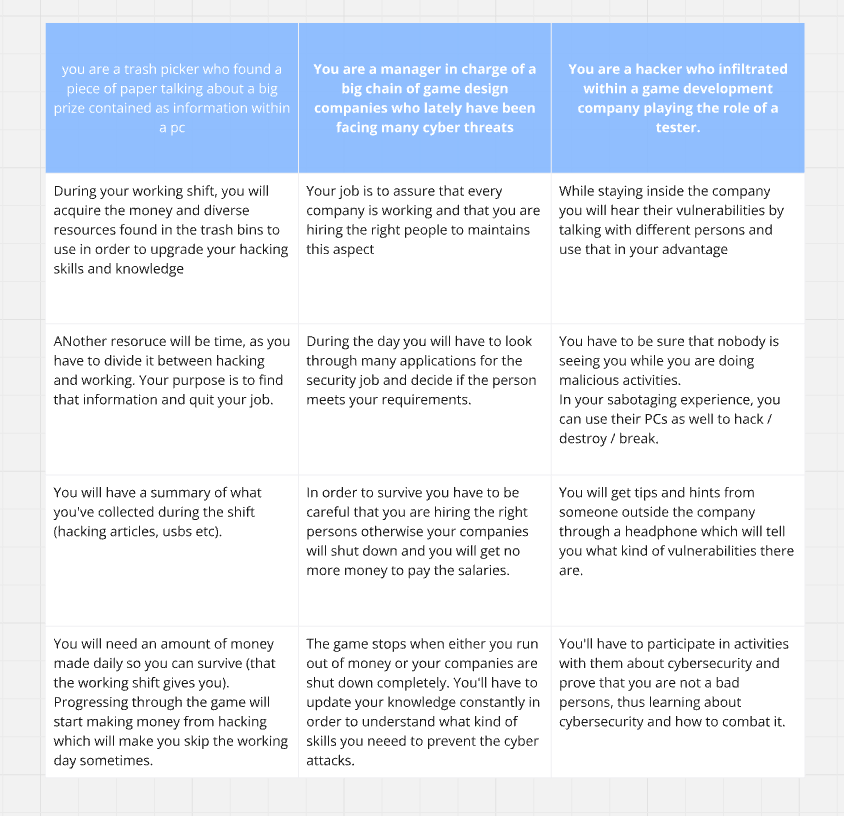
- 2.2. Weighted matrix
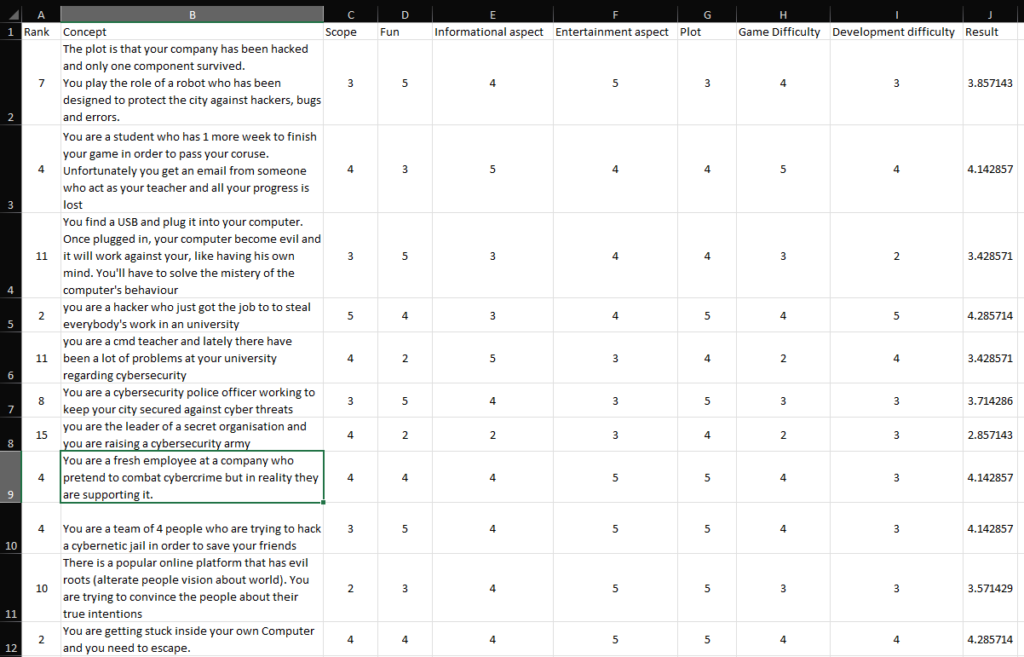
A weighted matrix was created to choose the best option among all the concepts. The weights used in the matrix are:
- Scope
Represents how likely the concept can be fully developed within the time left. Higher numbers indicate greater potential for completion. - Fun
It represents how much I’d enjoy developing the concept. Higher numbers mean
more fun. - Informational aspect
Indicates the potential to include cybersecurity-related details within the concept. Higher values reflect greater capacity to embed this aspect. - Entertainment aspect
It shows how entertaining the concept could be based on story and functions. Higher numbers mean higher potential to embed this aspect. - Plot
It shows how good the story is built. Higher numbers mean better story. - Game difficulty
It represents the adaptability aspect of the difficulty implied in the concept. Higher numbers mean a more suitable difficulty for the target audience. - Development difficulty
It represents the difficulty implied to develop the concept based on my experience. Higher numbers mean lower difficulty.
After the calibration, a personal top 5 has been made.

The top 5 has been sent to the client and I asked them to analyze the concepts and create their own top 5.

Finally, the 5 concepts have been sent to the target audience whose contacts I could obtain from the questionnaire.

Based on these factors, the final concept has been chosen.
3. Prototyping
The prototyping phase was carried out entirely in the Unity engine. This choice was based on my understanding of my own strengths and limitations, ensuring a smooth and productive development process during the remaining weeks of the graduation period. I determined that my programming skills weren’t strong enough to justify spending additional time creating a paper prototype or working on the concept in Figma.
- 3.1. Iteration 1
The first iteration contains a basic set-up that could make the game playable.
- 3.2. Iteration 2
Iteration 2 emphasizes a new prologue scene designed to show a proper introduction and add a bit more interactivity while getting through the dialogues. Once the prologue is done, the player will be transported to the main scene where a placeholder-room is assembled.
- 3.3. Iteration 3
This iteration emphasizes the first level of the prototype, the first floor of the company that the player is working in. In this iteration, a gameplay loop has been set.
4. Evaluation
- 4.1. Co-reflection
The first evaluation method involved weekly meetings with Gert and Mitchel. During these meetings, my clients provided feedback or advice based on the current development phase.
- 4.2. Test & Chill
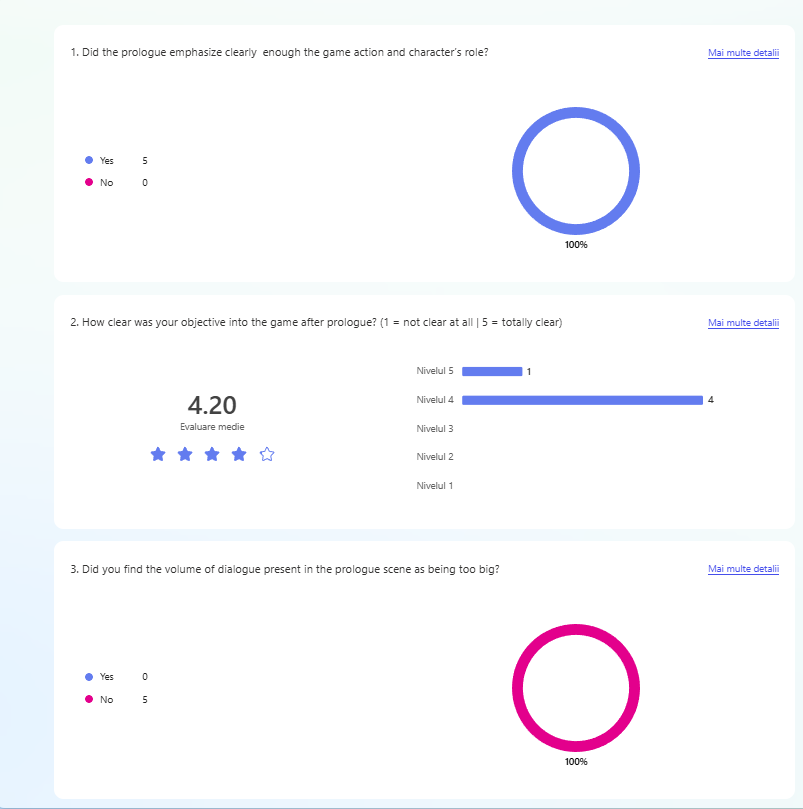
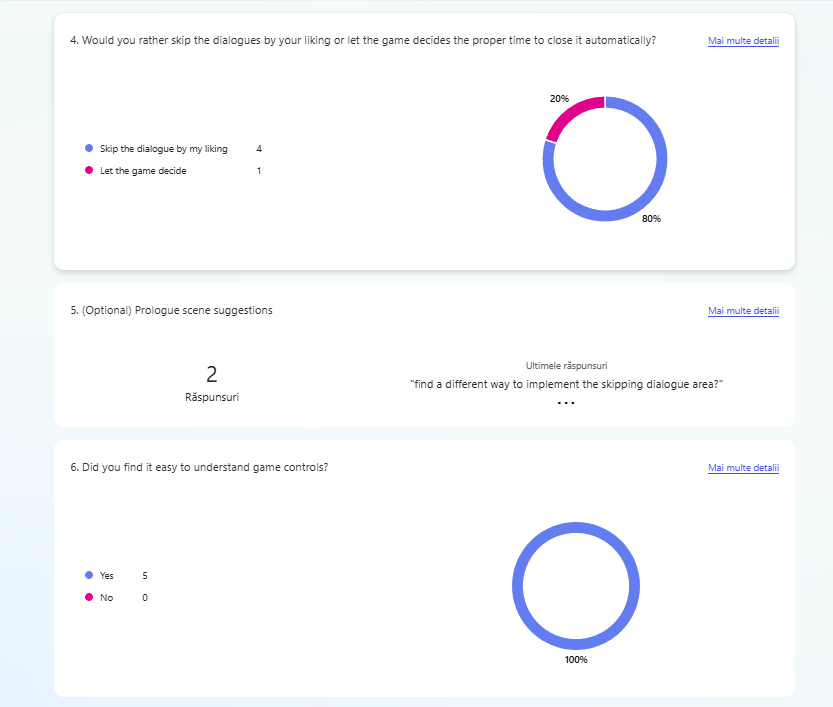
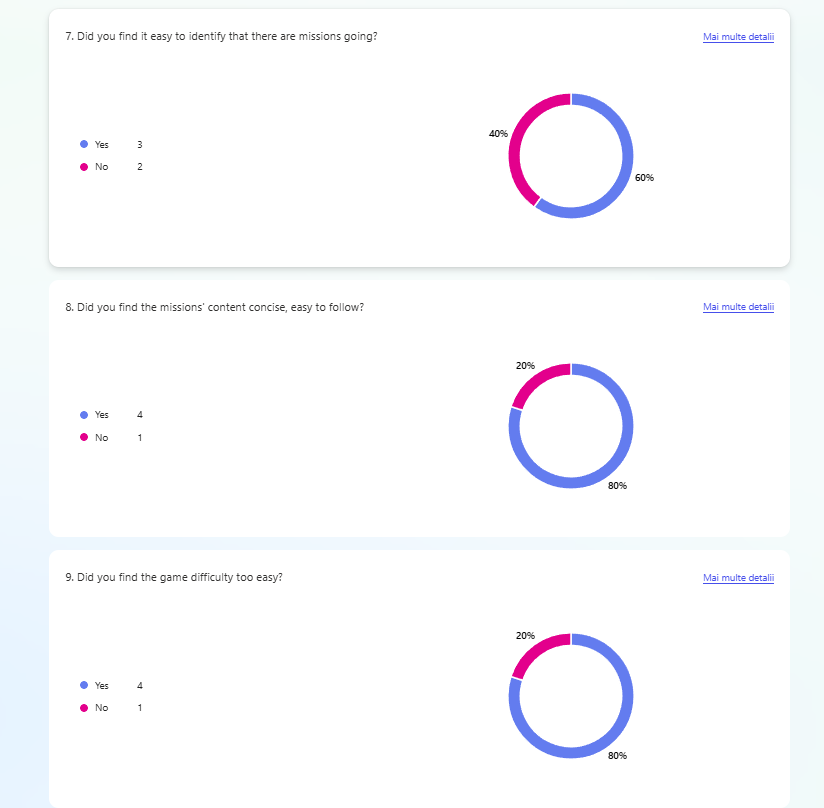
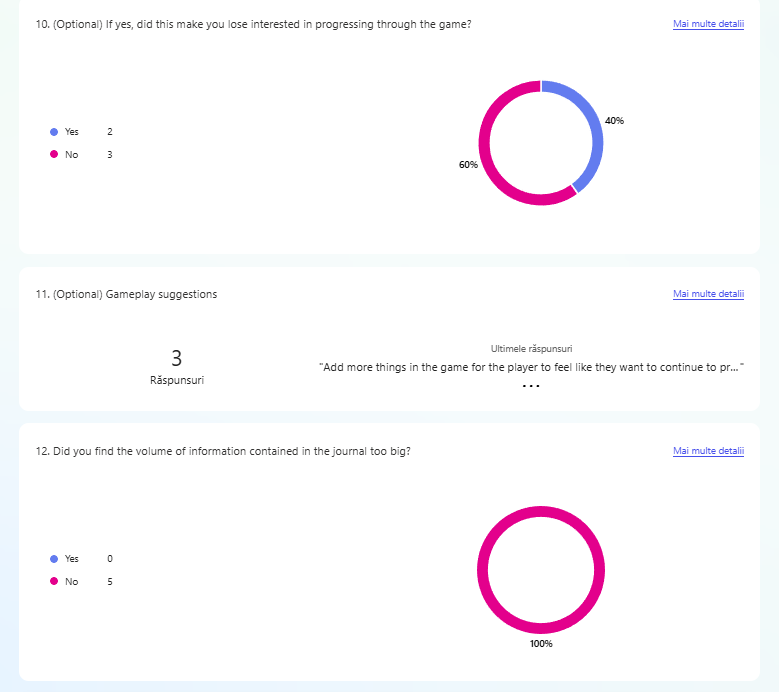
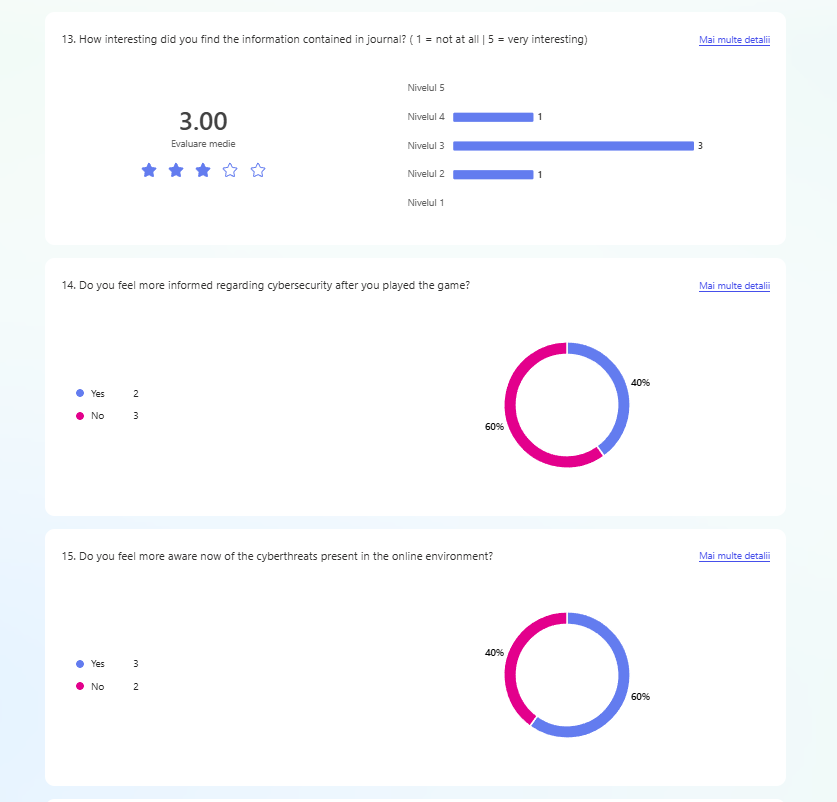
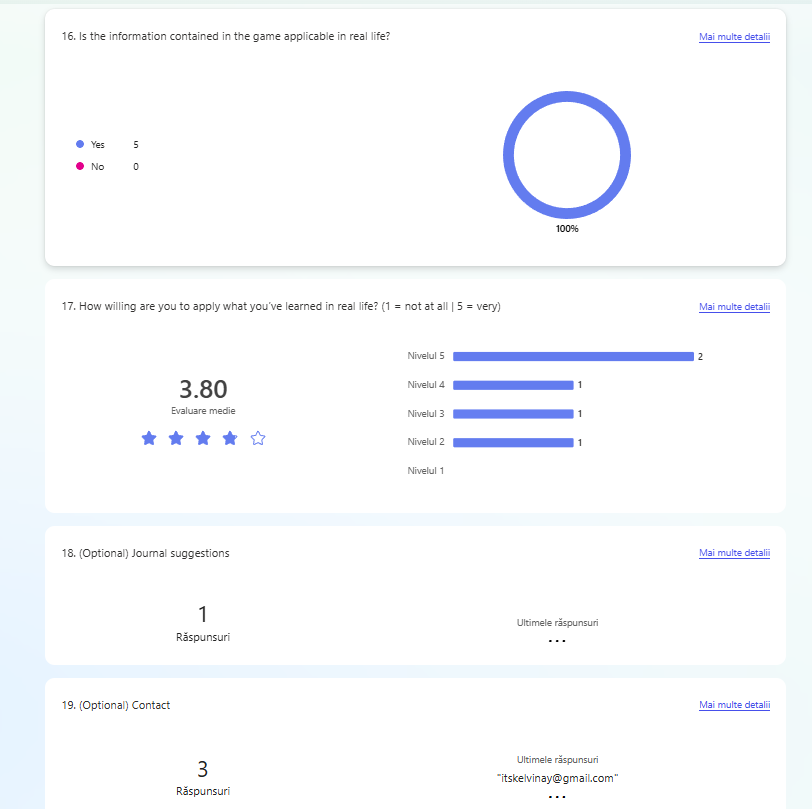
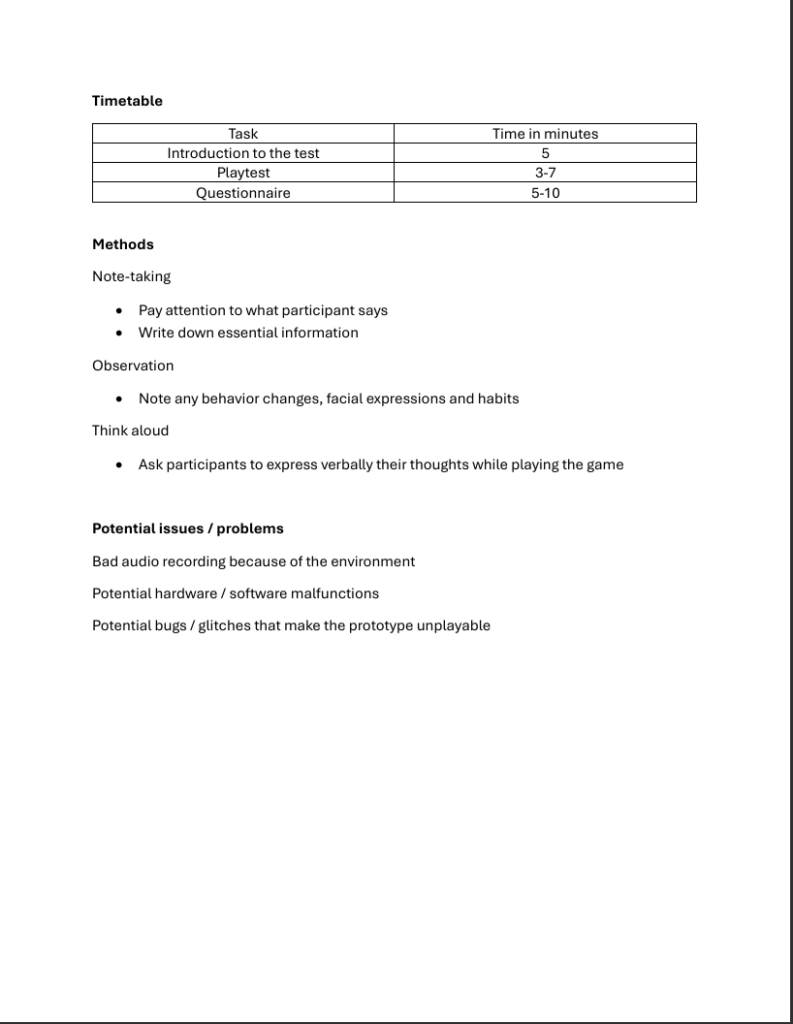
The second evaluation was done during the Test & Chill session at Hanze University of Applied Sciences. In this session, students came together to showcase their prototypes and exchange feedback. A total of 5 students participated in the initial phase of prototype testing.
For a concise, well-structured and efficient testing session, a testing plan has been created.

For a clear understanding of what the testers agree to by taking part in the testing session the testing form has been created.
The form has been presented to every participant In the testing session, and the session occurred only after the participant gave her / his consent and agreed with all the terms stated.

Every participant in the testing sessions has been asked to fill a questionnaire at the end of the session. The results are shown in the evidence and they have been used for the further implementation of the prototype.